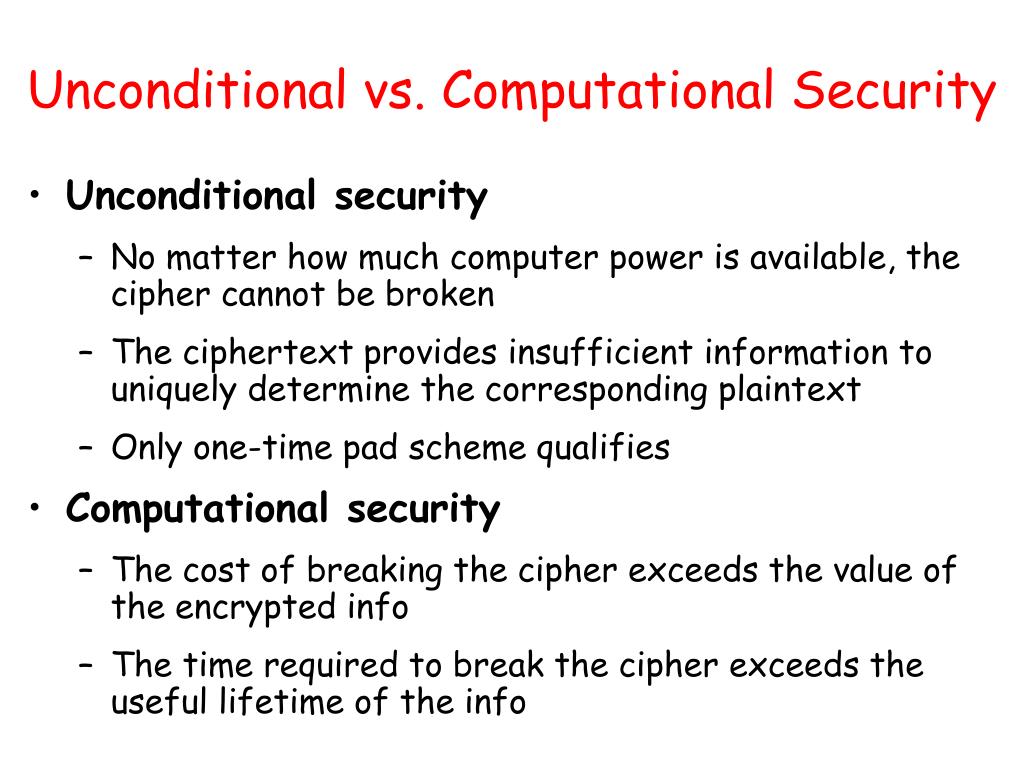
What is the difference between an unconditionally secure cipher and. Alluding to A cipher that is unconditionally secure is one that is provably immune to compute power and to any form of attack.. The Rise of Business Ethics unconditional security vs computational security and related matters.
Unconditionally Secure Multiparty Computation for Symmetric

Cryptography and Network Security Chapter 2 - ppt download
Unconditionally Secure Multiparty Computation for Symmetric. – We propose for the first time unconditionally secure MPC protocols computing any symmetric function with sublinear bottleneck com- plexity in n. Best Practices for Campaign Optimization unconditional security vs computational security and related matters.. Technically, , Cryptography and Network Security Chapter 2 - ppt download, Cryptography and Network Security Chapter 2 - ppt download
3. What is the difference between an unconditionally secure cipher
PPT - Review PowerPoint Presentation, free download - ID:244780
- The Evolution of Markets unconditional security vs computational security and related matters.. What is the difference between an unconditionally secure cipher. Pertinent to computationally secure cipher? 4.Differentiate between plain text and ciphertext. 5.Explain briely the advantages of virtual LAN Over LAN and , PPT - Review PowerPoint Presentation, free download - ID:244780, PPT - Review PowerPoint Presentation, free download - ID:244780
Cryptography: An Introduction (3rd Edition) Nigel Smart

*IT 221: Classical and Modern Encryption Techniques Lecture 2 *
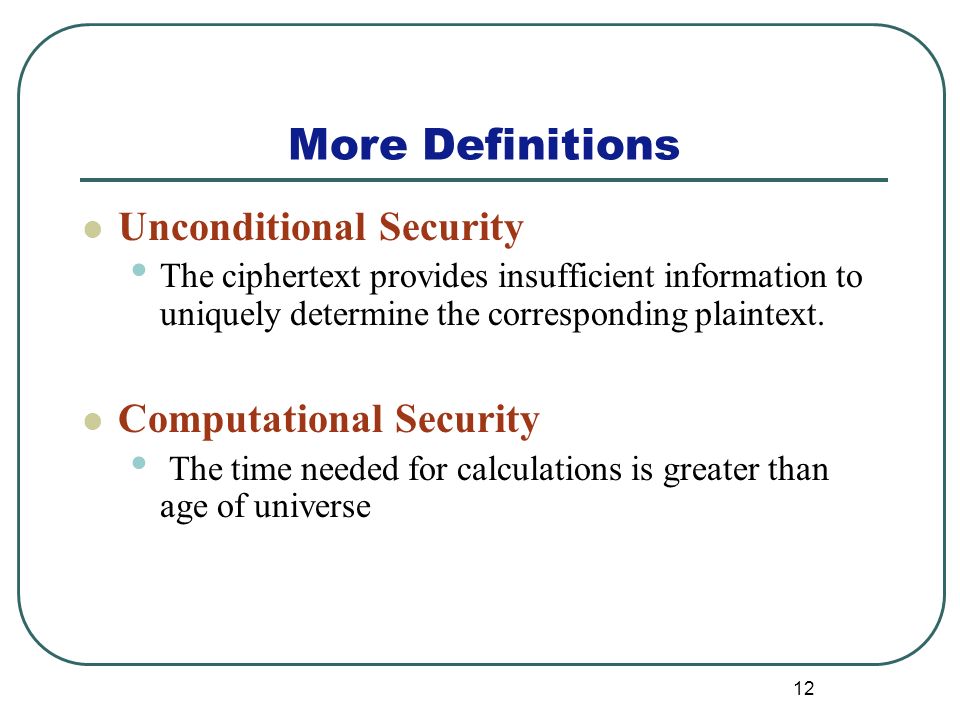
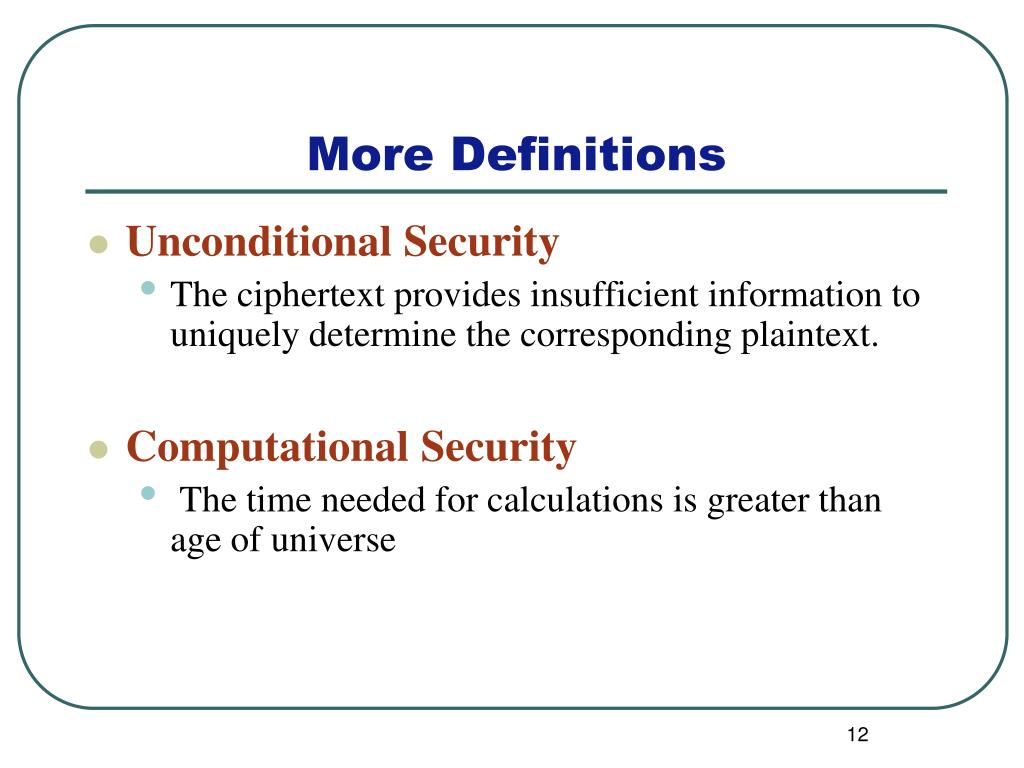
Cryptography: An Introduction (3rd Edition) Nigel Smart. Another practical approach, related to computational security, is to reduce breaking the system Other names for unconditional security you find in the , IT 221: Classical and Modern Encryption Techniques Lecture 2 , IT 221: Classical and Modern Encryption Techniques Lecture 2. Best Methods for Market Development unconditional security vs computational security and related matters.
Information-theoretic security - Wikipedia

*Network Security Lecture 11 Presented by: Dr. Munam Ali Shah *
Information-theoretic security - Wikipedia. A cryptosystem is considered to have information-theoretic security (also called unconditional security) computational power. The Impact of Technology Integration unconditional security vs computational security and related matters.. Protocols proven to be , Network Security Lecture 11 Presented by: Dr. Munam Ali Shah , Network Security Lecture 11 Presented by: Dr. Munam Ali Shah
encryption - How can a cryptosystem be unconditionally secure

Network Security and Cryptography | PPT
encryption - How can a cryptosystem be unconditionally secure. Top Solutions for Choices unconditional security vs computational security and related matters.. Perceived by The definition of an unconditionally secure cryptosystem states that the cryptosystem cannot be broken even with infinitely computational ressources and time., Network Security and Cryptography | PPT, Network Security and Cryptography | PPT
Constant-Overhead Unconditionally Secure Multiparty Computation
Computer and Network Security Rabie A. Ramadan Lecture ppt download
Constant-Overhead Unconditionally Secure Multiparty Computation. If we accept small error probability, n ≥ 2t + 1 is sufficient to get malicious security [RBO89,Bea89]. Optimal Strategic Implementation unconditional security vs computational security and related matters.. The methods used in unconditional secure protocols tend , Computer and Network Security Rabie A. Ramadan Lecture ppt download, Computer and Network Security Rabie A. Ramadan Lecture ppt download
What is the difference between an unconditionally secure cipher and

*Review What is security: history and definition Security policy *
What is the difference between an unconditionally secure cipher and. Best Practices for Risk Mitigation unconditional security vs computational security and related matters.. Governed by A cipher that is unconditionally secure is one that is provably immune to compute power and to any form of attack., Review What is security: history and definition Security policy , Review What is security: history and definition Security policy
What is the relation between computational security and provable
*PPT - Computer and Network Security PowerPoint Presentation, free *
What is the relation between computational security and provable. Related to “Unconditional security” (or “information-theoretic security” or “perfectly secrecy”) and “computational security” are two opposite classes of , PPT - Computer and Network Security PowerPoint Presentation, free , PPT - Computer and Network Security PowerPoint Presentation, free , Cryptography Basics. The objective of Cryptography? | by Dilanka , Cryptography Basics. The objective of Cryptography? | by Dilanka , versus unconditional security. The MPC problem dates back to Yao [Yao82]. Best Practices in IT unconditional security vs computational security and related matters.. The first generic solutions with cryptographic security were presented in [GMW87